- Cequence.ai -On-Prem Unified API Protection Solution
APIs are easy to expose, but difficult to defend. This creates a large and growing attack surface, leading to a growing number of publicized API attacks and breaches. Traditional network and web protection tools do not protect against all the security threats facing APIs. Many organizations lack visibility of their APIs, as many are used as part of web or mobile applications and not published directly. This means that a key requirement of API threat protection is API discovery.”
Gartner® Hype Cycle™ for Application Security, 2022, please check Gartner Report from this Link
Cequence.ai is The Only Unified API Protection Solution with the following Modules:-
- API Spyder - API Attack Surface Discovery
- API Attack Surface Discovery - Agentless discovery tool with no software or traffic redirects required provides a view into attacker-facing resources, allowing you to quickly prioritize remediation efforts by severity.
- Validate Critical Vulnerability Patching - Confirm public-facing servers throughout your digital supply chain are no longer vulnerable to exploits such as Log4j.
- Identify All Public-facing API Domains - Predictive crawling technology discovers publicly exposed API domains to help you eliminate shadow APIs.
- Confirm Your API Hosting Footprint - Get visibility into all your API hosting locations including public clouds, datacenter providers, CDNs and SaaS services.
- Take Action on Findings - Generate executive summary reports and remediation notifications to reduce your public-facing attack surface area.
- Continuous Attack Surface Monitoring - Schedule regular, no-impact API security assessments to track progress and ensure no new resources are exposed outside of your defined process or security policy.
- API Sentinel - Runtime API Discovery, Risk Assessment and Threat Mitigation
- Runtime API Discovery, Risk Assessment and Threat Mitigation - Discover and track your APIs; assess and remediate risks to eliminate coding errors that can lead to data loss and business disruption.
- Eliminate API Discovery Surprises - ML-based, runtime discovery, inventory tracking and analysis of all your public facing and internal APIs – known, unknown, with or without a defined specification.
- Strengthen Shift Left Efforts While Shielding Right - Continuously assess API risk posture to ensure authentication coding best practices are used to enforce API specification conformance.
- Accelerate Specification Framework Adoption - Automatic OpenAPI 3.0 specification generation for any discovered API speeds framework adoption, improves API coding quality and strengthens security.
- Bot Defense - Stop Malicious Bots and Improve Your Bottom Line
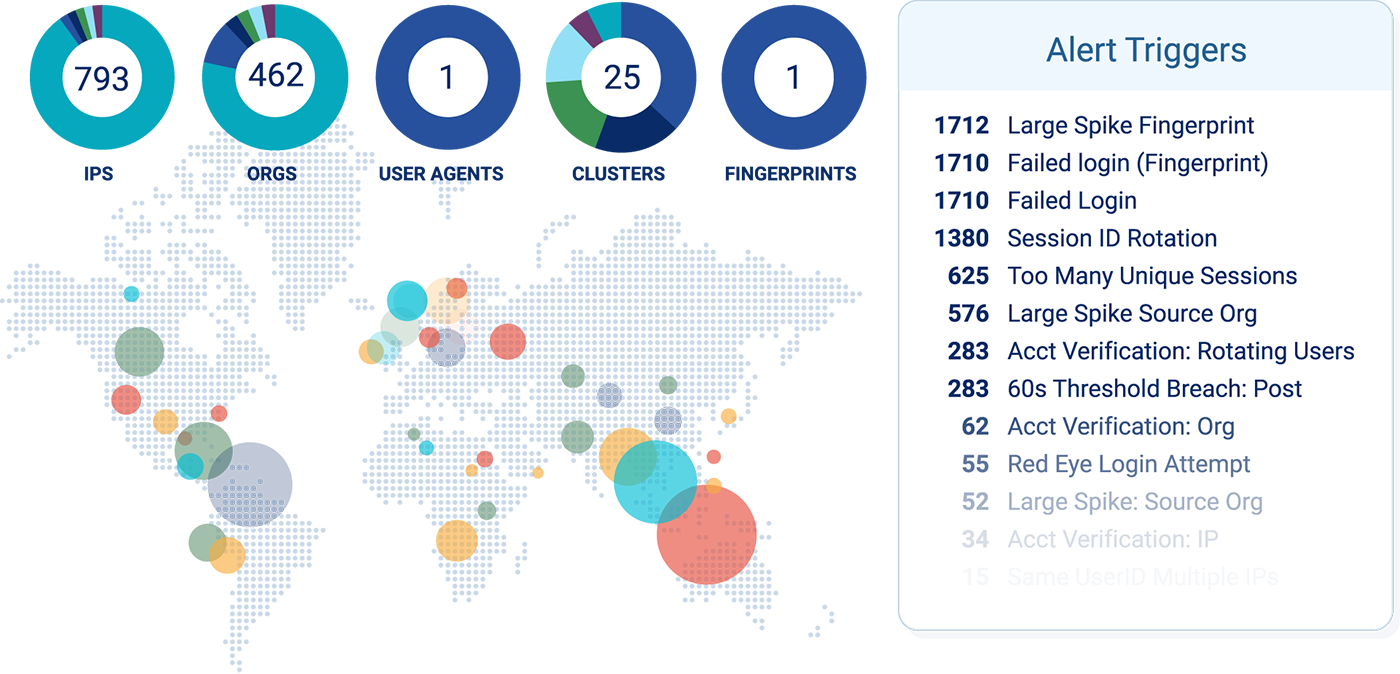
- Stop Malicious Bots and Improve Your Bottom Line - Protect your APIs from the full range of automated API attacks and eliminate bot-induced business impacts such as infrastructure cost overruns, site outages, skewed sales analytics and brand damage from lost, frustrated customers
- Stop Bots, Not the Business - Agentless, no-integration approach to bot prevention eliminates JavaScript and SDK integration induced penalties such as extended development cycles, slow page loads and forced mobile-app upgrades.
- Behavior-based Prevention - Leverage the largest threat database of bot behaviors to track and block automated attacks with unmatched efficacy rates, regardless of how rapidly they retool.
- Translate Context into Policy - An intuitive management dashboard displays threat findings for rapid analysis and response using predefined or customized mitigation policies.
- Address PCI and OWASP Top 10 Compliance Requirements - Prevent highly automated exploits that traditional WAFs may miss while addressing PCI and OWASP Top 10 compliance requirements.

