- Analyst1 - Threat Intelligence Platform
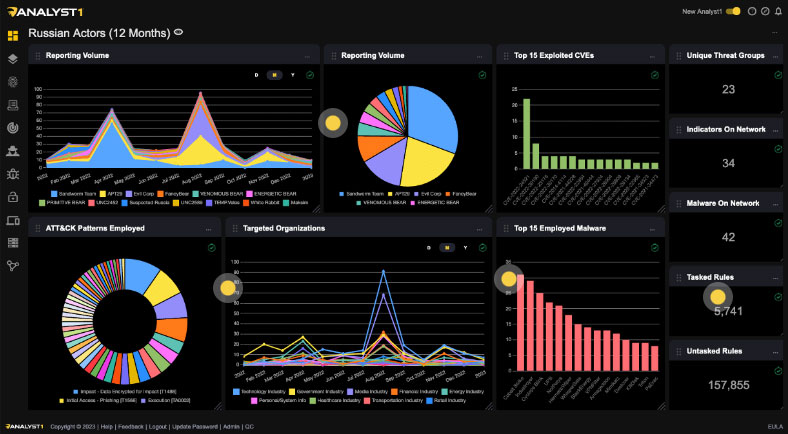
Analyst1'TIP is a powerful and innovative threat intelligence platform that helps you collect, process, analyze and act on cyber threat data from multiple sources. It enables you to:
- Automatically correlate data from open source, commercial and internal sources to create rich and relevant intelligence profiles of threat actors, malware families and attack techniques.
- Identify and prioritize your assets that are exposed to cyber threats by linking vulnerabilities to threat intelligence and endpoint visibility.
- Create and deploy defense rules to your security sensors and watchlists to prevent or detect cyber attacks before they cause damage.
- Centralize your security operations and oversight with a single platform that integrates with your existing security and identity products.
Analyst1'TIP is designed for cyber security analysts, incident responders, vulnerability analysts and CISOs who need a superior threat intelligence solution that can keep them ahead of the bad actors. Analyst1'TIP is more than just a data aggregator; it is a virtual Tier 1 analyst that works for you, not the other way around.
If you want to learn more about Analyst1'TIP and how it can improve your detection and response capabilities, request a demo today and see the difference for yourself.
Analyst1’s solution is a commercially available enterprise-scale Security Orchestration & Automated Response (SOAR) platform for threat hunting - malware perspective with built-in Threat Intelligence capabilities that employ supervised machine learning and natural language processing to automate cyber defense and reduce the burden on analysts. Analyst1 gives analysts a single pane of glass that makes them 7X more effective and efficient at identifying, triaging, prioritizing, and responding to cyber threats. Our customers successfully establish Analyst1 as their automated inter-system decision and data-sharing platform to integrate intelligence, countermeasures, threat context, and analyst decisions.
Analyst1 shifts an organization to a proactive defensive strategy by automating tier-one analyst functions to enable teams to focus on items that require more in-depth analysis. The Analyst1 platform has a bot — Analyst1 Bot (A1 Bot) — that automates the processes involved with collecting, correlating, and presenting actionable and contextual content from multiple data sources. The automation provided by the A1 Bot reduces the time to identify threats, evaluate your threat exposure, discover malicious activity, prioritize response, and manage mitigations.
-
-
- Automate identification, collection, and correlation of diverse information
- Aggregate threat intelligence from multiple sources
- Enrich threat intelligence to gather further data and context
- Retain threat intelligence to support forensic investigations
- Enable analysis and sharing of threat intelligence
- Send Indicators Of Compromise (IOCs) to Security Information and Event Management (SIEM) systems
- Automate the categorization and correlation of threat intelligence (ATT&CK, actors, malware, dates, etc)
- Automate the creation of threat actor profiles and malware profiles
- Identify the organization’s assets and systems with vulnerabilities known to be exploited by threat actors
- Enforce all intelligence to be portion marked with sourced classification and dissemination controls
- Trend detections of threats, malware, CVE exploits, and the presence of IOC's over time
- Enrich alerts with context (corresponding threat, malware, CVEs, IOCs, and why a rule was created)
- Author, test, deploy, and manage rules across intrusion detection/prevention systems
- Automate incident response workflows (tickets and security controls)
- Provide the threat context and analyst insight to support the data needed for automated workflows
- Correlate different names of threat and malware across security providers
- Deploy onto incident response fly away kits to provide context of security events
-


