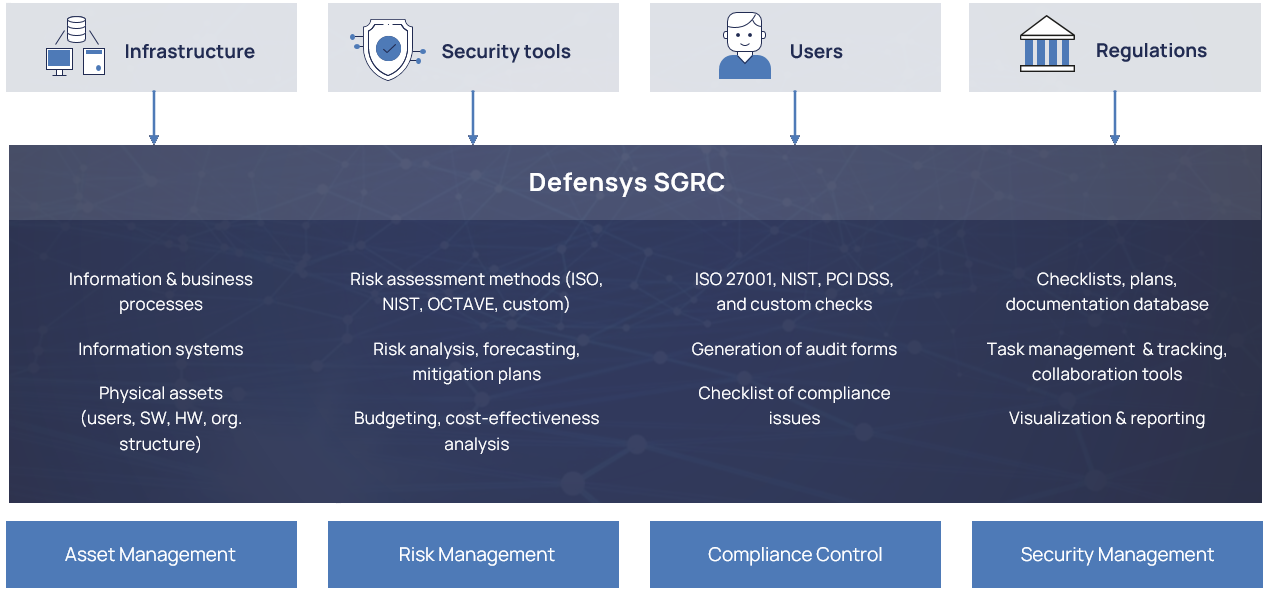
- Defensys Security GRC Platform (SGRC)
- Defensys SGRC allows calculating risks by using one of the built-in methodologies and keeping eye on risk level changes, producing a risk mitigation action plan and controlling its implementation status.
- The software enables automated security audits and checks for compliance to industry security standards and best practices. In addition to ISO 27001, PCI DSS v.3.2, SWIFT and NIST which are available out-of-box, Defensys SGRC supports import of proprietary standards, risk methodologies and threat databases.
- For instance, for our respected customers from GCC region SGRC supports out-of-the-box the whole list of frameworks that can be found below.
Defensys Security GRC Platform (SGRC) Key Benefits:-
- Insight into the company’s information security level, effectiveness of the implemented security measures, and compliance level to industry standards and regulatory requirements.
- Optimized resources for risk management and compliance control through risk assessment and audit automation.
- Reduced cybersecurity risks thanks to increased employee awareness.
- Estimated probability of information security threats and potential losses incorporated into company’s operational risks.
- A holistic view of the company’s information security system for planning and prioritizing of measures, budgeting and decision making.
Information Security Management:-
- Defensys SGRC Platform collects and stores data about information security processes and enables its visualization facilitating decision making, prioritization of required measures and budgeting.
- Built-in metrics help to track the performance of the security team and monitor the overall level of information security within the company or organization, measure effectiveness of realized initiatives and manage compliance to standards, best practices and regulations.
Risk Assessment & Management
- Risk management is one of the key processes for security information. Defensys SGRC allows calculating direct and indirect risks associated with information security by using one of the built-in methodologies including ISO 27005, NIST, OCTAVE, FAIR, basic 3-level schemes and Defensys proprietary methodology. Custom risk assessment methodologies are also supported.
- Asset value, implemented security controls and measures, and historical risk rates are taken into account while performing risk assessment.
- All the needed content for the cyber security risk assessment is available out-of-the-box just after the installation of the system. These are lists of threats, threat actors, security controls and their interconnections – our experience collected for more than 10 years on different markets.
Risk Maps & Mitigation Plans
- Defensys SGRC automatically generates a risk map indicating
- risk sources and factors,
- required security measures,
- related incidents,
- mitigation steps,
- historical risk level values.
- Risk map data is automatically included into consecutive assessments.
- The software also produces a risk mitigation plan with estimated cost and effectiveness of the risk mitigation strategy chosen. It also allows to keep track of the implemented measures and monitor the risk level changes over time.
Audits and Compliance campaigns control
- Information security audits are necessary to keep an eye and control the state of information security in the organization. Defensys SGRC Platform helps to build comprehensive compliance control system with regulatory and industry standards + supports proprietary security standards and check-lists. Out-of-the-box users can work with the following frameworks:
-
- ISO 27001
- GDPR
- PCI DSS
- SWIFT CSP
- NESA
- UAE IA Regulation
- SAMA Frameworks
- MAS TRM
- Shariah Governance Framework
- KSA NCA Essential Cybersecurity Controls
- Upon the end of an audit the software calculates an overall index of compliance and generates a report indicating the status of each requirement. This report helps in defining steps needed to improve the compliance.

