- Deepfence - Cloud native workload protection - Kubernetes, virtual machines, and serverless environments
 Deepfence Inc is a company that provides a cloud native workload protection platform that is designed to stop today's and tomorrow's sophisticated cyber-attacks. The platform leverages security observability, deep packet inspection, and runtime protection to detect and prevent vulnerabilities, misconfigurations, malware, and exploits in cloud native applications. Deepfence's platform supports Kubernetes, virtual machines, and serverless environments, and offers both open source and enterprise solutions. Deepfence helps security teams reduce alert fatigue, prioritize risk, and respond to threats faster and more effectively.
Deepfence Inc is a company that provides a cloud native workload protection platform that is designed to stop today's and tomorrow's sophisticated cyber-attacks. The platform leverages security observability, deep packet inspection, and runtime protection to detect and prevent vulnerabilities, misconfigurations, malware, and exploits in cloud native applications. Deepfence's platform supports Kubernetes, virtual machines, and serverless environments, and offers both open source and enterprise solutions. Deepfence helps security teams reduce alert fatigue, prioritize risk, and respond to threats faster and more effectively.
We are excited to introduce you to Deepfence Inc, the Cloud Native Workload Protection Platform purpose-built to stop today's and tomorrow's sophisticated cyber-attacks.
Deepfence is a next-generation security solution that leverages artificial intelligence and micro-segmentation to protect your cloud-native applications and infrastructure from advanced threats. Deepfence provides comprehensive visibility, detection, prevention, and response capabilities across your entire cloud environment, including containers, Kubernetes, serverless, and virtual machines.
Deepfence Inc is a company that specializes in providing security solutions for cloud native environments, such as Kubernetes, Docker, AWS, Azure, GCP, and more. Their platform leverages artificial intelligence and machine learning to detect and prevent attacks across the entire application lifecycle, from development to deployment to runtime.
With Deepfence, you can:
- Gain real-time visibility into your cloud assets and their dependencies
- Detect and block malicious activities and vulnerabilities at runtime
- Isolate and quarantine compromised workloads automatically
- Investigate and remediate incidents with forensic evidence and actionable insights
- Integrate seamlessly with your existing DevOps tools and workflows
Deepfence is easy to deploy and manage, with no agents or kernel modules required. You can start securing your cloud workloads in minutes, with minimal impact on performance and scalability.
The benefits of using Deepfence:
- You can scan and prioritize cloud security alerts with ThreatMapper, Deepfence's enterprise-grade open-source tool that helps you build a ThreatGraph of your cloud environment and reduce 97% of the noise from security scan results.
- You can get runtime protection at cloud scale with ThreatStryker, Deepfence's enterprise solution that performs deep packet inspection of inter-container and inter-virtual machine traffic without adding additional latency to your data path.
- You can correlate, understand, and respond to vulnerabilities, exposed secrets, cloud misconfigurations, and malware using runtime context to evaluate exploitability and paint a holistic picture of your security posture and risk.
Deepfence ThreatStryker observes, correlates, learns, and acts to protect your applications and keep you one step ahead of attackers. Use ThreatStryker to:-
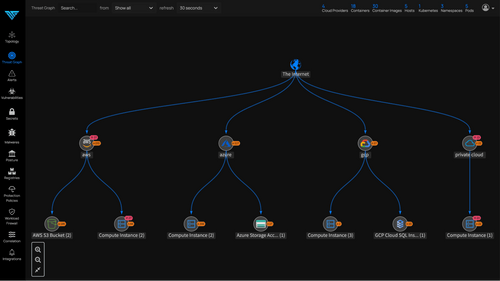
- Map the presence of threats - discovers all running containers, processes, and online hosts, and presents a live and interactive color-coded view of the topology.
- Observe anomalies in application behavior and network traffic
- Audit - Scan build artifacts for vulnerabilities during Continuous Integration
- Monitor - Continuous scanning of production to identify newly-published vulnerabilities
- Compliance - Evaluate compliance against community and industry standard benchmarks
- Deploy targeted remediation against active threats - takes appropriate and contained remedial action. Tainted workloads are deleted, frozen, or restarted, sources of attack traffic are temporarily or permanently blocked
- Prioritize Vulnerabilities - Ranking of vulnerabilities based on exploitability and proximity to attack surface
- Alert on Attack - Cyber-Kill-Chain modeling of attack, from recon through spread to exfiltration
- Remediate with Automatic quarantine of compromised workloads in event of compromise

